Large Language Models (LLMs) and AI agents have fundamentally changed how we interact with information and services online. Organizations across industries are now seeking standardized, scalable ways to expose their products and services to this “new user” — the AI agent.
The Model Context Protocol (MCP), developed and open-sourced by Anthropic in November 2024, is emerging as a promising standard to streamline and scale connectivity in the agentic AI era. However, taking MCP servers into production introduces significant identity and security challenges.
This blogpost provides an overview of MCP, outlines the core security hurdles enterprises face with MCP, and provides actionable identity recommendations to secure MCP ecosystems.
What is MCP? – A Quick Overview
The Model Context Protocol (MCP) provides a standardized way for LLMs and AI agents to connect with external data sources and tools, akin to a “universal remote” for AI. The protocol:
- Defines a format to specify tools (functions) across any AI system
- Provides a protocol for discovering and executing available tools
- Creates a universal format that allows any AI app to use any tool without custom integration code
Core MCP components
To understand how the Message Context Protocol (MCP) functions in practice, it’s important to look at its core components. MCP is built on a modular architecture that enables seamless interaction between applications and external tools or services. This section breaks down the three fundamental building blocks that make up every MCP integration: the client, the server, and the transport layer that connects them.
- MCP client: Embedded within a host application,such as a large language model (LLM), the client manages connections to MCP servers. For example, Claude Desktop includes an integrated MCP client.
- MCP server: Provides the context and capabilities that clients can discover, request, and use (e.g., the Stripe MCP server)
- Transport Layer: Defines how clients and servers communicate. Locally hosted servers typically use standard input/output, while remote servers rely on HTTP and SSE (Server-Sent Events) for real-time data exchange.
Here’s how the core MCP components interact in a typical architecture. A host application equipped with an MCP client (e.g., Claude, IDEs, or other tools) can connect to multiple MCP servers — each exposing specific capabilities or data sources. Communication between clients and servers is handled via the MCP protocol, using either local or remote transport methods.
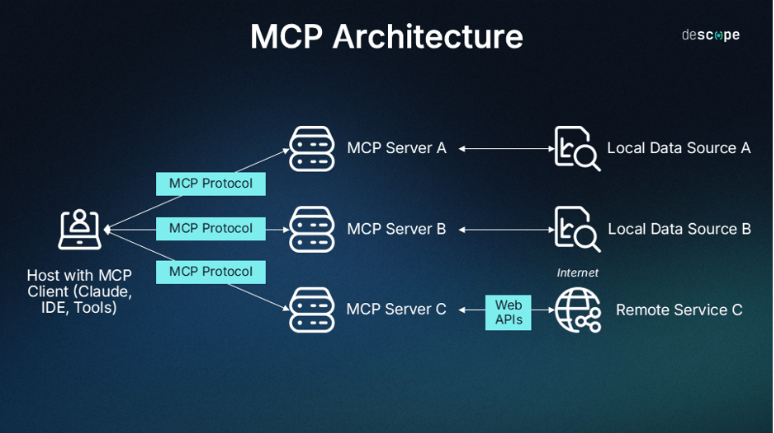
While any organization can build an MCP server, implementing one securely and at scale is a complex task.
Enterprise Challenges in MCP Adoption
Implementing MCP introduces several identity-related hurdles. These are the most common challenges enterprise teams face:
OAuth 2.1 Compliance
The MCP specification recommends OAuth 2.1 “with appropriate security measures for both confidential and public clients”. This means enterprises must invest expertise in implementing and maintaining Proof Key for Code Exchange (PKCE), Dynamic Client Registration (DCR), and other nuanced OAuth flows.
Scopes and Permissions
The permission model for enterprise MCP servers requires scope-level granularity rather than traditional API-level access controls. For example, a CRM MCP server might expose tools to “read contacts data,” “update deal records,” and “export contact lists”, each requiring different scopes even though they all access the same underlying API.
Token Lifecycle Management
Enterprises need systematic ways to check whether users have the required tokens and what level of access those tokens grant to specific MCP servers and the tools within them. Managing, storing, and refreshing these tokens is an ongoing engineering and IT burden.
Auth and SSO Integration
Enterprise MCP servers need to be protected via user authentication – ideally with Single Sign-On (SSO) for internal users and B2B partners. However, native SSO support is currently absent from the MCP specification, requiring custom implementations or workarounds.
Lack of Visibility
As AI agents begin to outnumber human users, enterprises need granular, centralized visibility into their lifecycle. This includes agent registration, verification status, granted scopes, and audit trails of all associated identity actions. Without this, organizations face increased security and compliance risks.
Best Practices to Secure MCP Servers
Here are some actionable steps enterprises can follow to improve the security and production-readiness of their MCP servers:
Authorization Server Configuration
Treat MCP servers as Resource Servers only, while dedicated external Authorization Servers should be used to handle OAuth flows. Leverage your existing enterprise identity provider (IdP) and configure MCP servers to reference the issuer’s metadata directly. This allows MCP clients to reliably locate and interact with your IdP for token exchange.
Scoping and Permission Management
Validate scopes at the tool or function level, as MCP tool calls may not map one-to-one with APIs. This minimizes friction for AI agents without inundating users with scope-related consent prompts. Grant minimum necessary scopes to AI agents for their intended task and expand only when required. Design user-facing consent management screens that clearly show what scopes are being requested on behalf of the user.
Dynamic Client Registration (DCR) Hardening Tips
Restrict DCR to known IP ranges or require VPN access. Implement allowlists for redirect URI domains, accepting only registrations from clients using approved callback URLs. Use separate verification processes for public and confidential clients. Configure sessions to be short-lived for DCR-registered clients, enforcing re-authentication at regular intervals to limit the impact of compromised credentials.
Conclusion
Enterprises can drive lasting business growth with MCP servers, but only if these servers are implemented with the proper identity and security guardrails without sacrificing the protocol’s benefits.
At iC Consult, we help enterprises implement secure, scalable MCP architectures. The Descope Agentic Identity Hub and Agentic Identity Control Plane provide a suite of capabilities that help organizations secure MCP servers with OAuth 2.1 authorization, consent management, user auth and SSO, and scope-based access controls.
Looking to secure your MCP deployment? Contact us today to fortify your agentic AI and MCP deployments.
