Managing privileged access is crucial for organizations looking to protect their critical systems and sensitive data. As cyber threats continue to evolve, ensuring your Privileged Access Management (PAM) strategy keeps pace with your organization’s needs is vital.
But how can you assess where your PAM strategy stands — and what steps are needed to improve it? This is where the PAM Maturity Model comes in: a structured framework designed to help organizations evaluate their current practices and identify the path to building a fully optimized and secure PAM program.
In this blog post, we’ll introduce the PAM Maturity Model, break down its five stages, and help you identify where your organization currently stands. You’ll also gain practical insights on how to advance your PAM strategy, ensuring it’s equipped to combat today’s evolving cyber threats.
What is the PAM Maturity Model?
The PAM Maturity Model is a structured framework that outlines stages of PAM development. It provides a clear roadmap for organizations to assess their current security practices, set priorities, and build a strategic path toward improving privileged access management.
Implementing all PAM capabilities at once can be overwhelming and may lead to friction with end users. The PAM Maturity Model helps organizations take a phased approach, focusing on incremental improvements that align with their security goals and operational needs.
While there’s no universally standardized PAM Maturity Model, our team at iC Consult has leveraged extensive experience — with over 200 successful PAM projects — to develop a proven five-stage framework. This model reflects best practices from real-world implementations and offers practical guidance for building a secure, scalable PAM program.
Let’s dive into the five stages and explore how they can guide your organization toward achieving identity security.
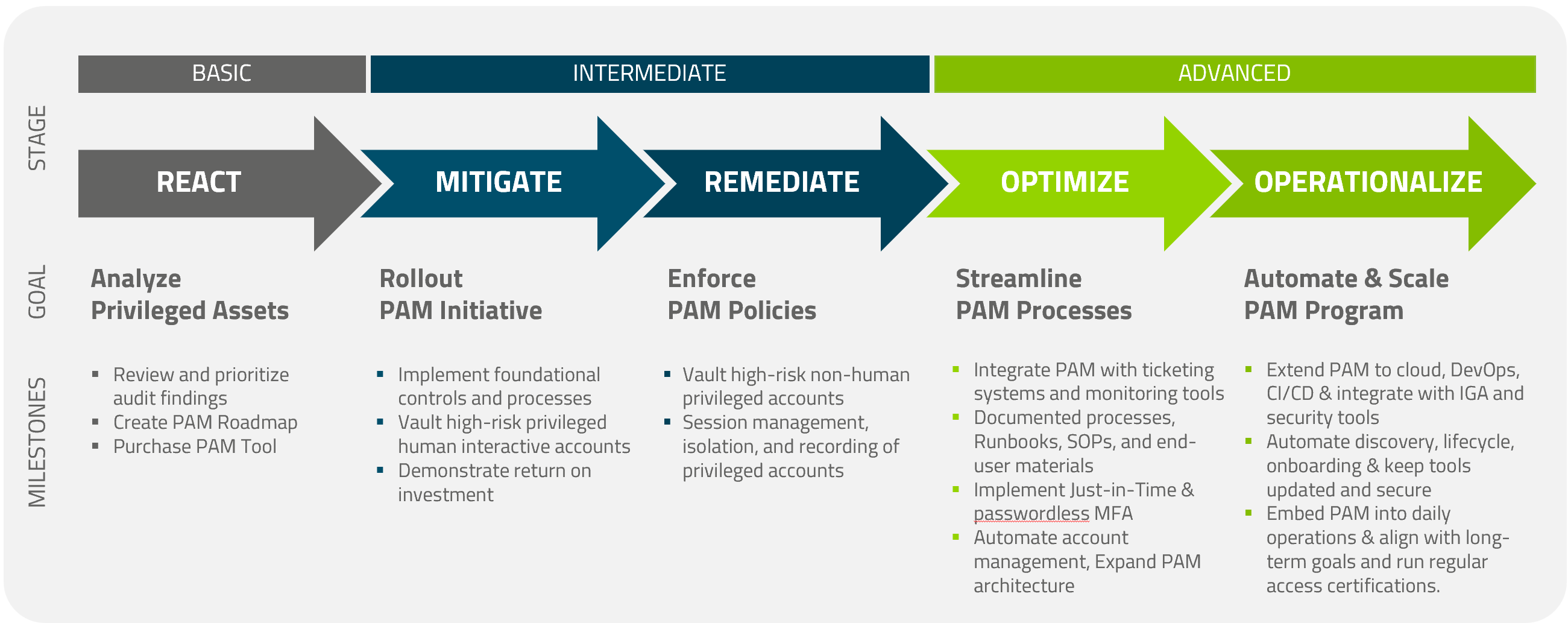
Stage 1: React – Analyzing Privileged Assets
Organizations in the “React” stage often find themselves caught off guard by the need to address urgent security or audit requirements. Without a clear understanding of privileged access management (PAM), they struggle to define what “privileged access” truly means and how to manage it effectively. At this point, many businesses lack a formal PAM program entirely, or if one exists, it’s typically in its infancy—only implemented for specific use cases. Processes are manual, and the PAM tool is often selected or deployed without integration into other key systems like Identity Governance and Administration (IGA). This fragmented approach leaves much of the potential of PAM untapped, and the overall goals for the program remain undefined.
Priorities for the “React” Stage
At this stage, the priority should be to establish a solid foundation: clearly defining privileged accounts, reviewing and prioritizing any outstanding security or audit issues, and developing an actionable plan to address them. Organizations should begin evaluating PAM tools and formulate a strategy for their deployment. Finally, crafting a PAM roadmap during the “React” stage will set the stage for building a robust and scalable PAM program moving forward.
Stage 2: Mitigate – Rolling out a PAM Initiative
At this stage, organizations have deployed or are in the process of deploying a PAM tool, but the program is still in its early phases. Short-term goals are established, primarily focusing on securing a limited set of credentials. Administrators can manage day-to-day tasks for the current user groups, but the process is largely manual, and the identification and securing of additional groups and accounts remain a challenge. While the foundations are in place, the PAM solution is not yet fully integrated, and the scope of coverage is limited to a small subset of high-risk privileged accounts.
Priorities for the “Mitigate” Stage
In the “Mitigate” stage, organizations should focus on strengthening their PAM program by refining foundational controls and expanding its reach. The PAM tool should be fully deployed and integrated into the environment, with clear processes established for managing privileged access. High-risk privileged human interactive accounts should be secured by vaulting their credentials to ensure their protection. Alongside this, it’s important to create key metrics that can demonstrate the return on investment (ROI) of the PAM solution, helping to show its value to stakeholders.
The next priority is to begin discovering and securing non-human privileged accounts, such as service accounts, applications, and automation tools like RPA. This step will expand the scope of the PAM program beyond human users. As the program matures, it’s essential to continuously reassess the privileged access landscape, identifying new opportunities for securing additional accounts. This includes vaulting new subsets of privileged accounts and leveraging additional security features offered by the PAM tool, such as session recording and isolation, to enhance monitoring and control. Finally, managing non-human accounts, including applications, vulnerability scanners, and robotic process automation (RPA) tools, should be integrated into the PAM solution to ensure comprehensive coverage and robust protection across all privileged access points.
Stage 3: Remediate – Enforcing PAM Policies
In the “Remediate” stage, the organization shifts its focus to addressing previously identified gaps and vulnerabilities in its privileged access management strategy. Account lifecycle processes, along with incident response protocols, are now more comprehensive, and organizations are actively working on closing security loopholes. The focus is on improving the management of privileged accounts, with session management, recording, and isolation becoming central to reducing risks. Manual efforts, such as onboarding non-human accounts, are still in play, but there’s a strong push toward automating and enhancing these processes for better efficiency and control.
Priorities for the “Remediate” Stage
The primary focus in the “Remediate” stage should be formalizing policies and processes to ensure a more mature and comprehensive approach to PAM. It’s critical to revisit the PAM roadmap to assess progress, ensuring alignment with organizational security goals. High-risk non-human accounts should be vaulted to further protect these critical access points, and the management of privileged sessions should be enhanced through improved isolation and recording mechanisms.
Account lifecycle management processes must be fully defined, with a clear framework for onboarding, offboarding, and managing privileged access across the organization. Additionally, a baseline for incident response processes and protocols should be established to ensure timely and effective reactions to security incidents. Implementing session monitoring will further strengthen control over privileged access, making it easier to detect and respond to any suspicious activities. By securing high-risk non-human privileged accounts and enhancing session management, isolation, and recording, the organization will significantly improve its overall security posture.
Stage 4: Optimize – Streamline PAM Processes
In the “Optimize” stage, organizations focus on fine-tuning their PAM practices for greater efficiency and effectiveness. The processes are now well-established and automated, significantly streamlining day-to-day operations. Automation plays a key role in maintaining existing user groups and ensuring that workflows run smoothly without manual intervention. The PAM solution is leveraged not only for access management but also for auditing, providing valuable data to enhance security operations.
Security controls are strengthened with advanced measures such as Just-in-Time (JIT) provisioning and password-less multi-factor authentication (MFA), both of which reduce the risk of credential misuse and unauthorized access. Integration with external systems, such as ticketing systems and monitoring tools, further optimizes the process by automating access requests and enabling real-time threat detection. This integration ensures that the PAM program remains agile and responsive to emerging security threats.
Priorities for the “Optimize” Stage
The next priority is to extend the PAM solution into cloud infrastructure and DevOps tools, ensuring that privileged access management is consistent across all environments. Periodic assessments should be conducted to ensure that the PAM program aligns with the established roadmap, making adjustments as necessary to address any emerging needs or gaps.
To further optimize the PAM program, focus on the following:
- Integrate PAM with Ticketing Systems and Monitoring Tools: Automate privileged access requests by integrating PAM with ticketing systems (e.g., ServiceNow) and monitoring tools such as SIEM and PTA. This will streamline access control and facilitate real-time threat detection.
- Document Processes, Runbooks, SOPs, and End-User Materials: Ensure that all processes are well-documented, with clear Runbooks, Standard Operating Procedures (SOPs), and materials available for end-users, making it easier for the PAM team and users to follow the established procedures.
- Implement JIT and Passwordless MFA: Enforce advanced security measures like Just-in-Time (JIT) provisioning and password-less multi-factor authentication (MFA) to further minimize credential misuse and unauthorized access.
- Automate Account Onboarding and Removal: Automate the process of onboarding and offboarding privileged accounts, ensuring that all accounts are managed consistently and efficiently.
- Expand PAM Architecture for Automation and Availability: Continue to expand the PAM architecture to support further automation and enhance availability, ensuring that the solution scales with the organization’s needs.
By focusing on these priorities, organizations can significantly improve the efficiency, security, and scalability of their PAM program, ultimately ensuring a mature, automated, and responsive privileged access management system.
Stage 5: Operationalize – Automate and Scale Your PAM Program
At this stage, the PAM program is fully embedded into the organization’s operations, ensuring ongoing relevance and adaptability as systems and applications evolve. The PAM tool is now integrated into end-user workflows, allowing for seamless interactions. Regular engagement with end users and audit teams ensures that the program stays proactive and aligned with the organization’s security and compliance requirements. The PAM solution communicates effectively with other IGA tools and security systems, relaying critical real-time information related to provisioning, threat management, and privilege escalation.
Priorities for the “Operationalize” Stage
To fully operationalize the PAM program, organizations need to focus on extending its reach, automating key processes, and ensuring it is ingrained in the daily operations of the organization. This involves expanding the PAM solution into new areas like cloud infrastructure, DevOps tools, and CI/CD pipelines, and automating discovery and account lifecycle processes to streamline management.
Key actions to prioritize include:
- Expand PAM into Cloud Infrastructure, DevOps Tools, and Pipelines: Broaden the scope of the PAM solution to cover cloud environments, DevOps tools, and automation pipelines, ensuring that all privileged access is secured across modern infrastructures.
- Automate Discovery & Account Lifecycle Management: Leverage automation to discover privileged accounts and manage their lifecycle, integrating these processes with the organization’s IGA solution or using APIs and scripts for efficiency.
- Mature and Sustain the PAM Program: Ensure the PAM program is sustainable by embedding it into the organization’s culture and processes. Establish long-term goals and policies that support continuous improvement and alignment with the organization’s overall security strategy.
- Formalize End-User and Admin Procedures: Clearly define and document processes for both end users and administrators, making it easy for both groups to follow best practices and ensure compliance.
- Automate Onboarding of Accounts and Users: Implement automation for onboarding and offboarding privileged accounts and users, reducing the risk of human error and increasing efficiency.
- Maintain PAM Tool Security and Currency: Keep the PAM solution up-to-date with regular patches, upgrades, and security assessments, ensuring there are no open vulnerabilities and that the tool continues to provide robust protection.
- Align PAM Goals with the Roadmap: Establish long-term PAM goals that are aligned with the overarching PAM roadmap, ensuring the program evolves to meet emerging security challenges.
- Implement Access Certifications: Conduct regular access certifications to ensure that only authorized users have privileged access, maintaining compliance and minimizing unnecessary risk.
By focusing on these priorities, organizations can ensure that their PAM program becomes a mature, integrated, and sustainable part of their security infrastructure, continuously protecting critical systems while adapting to future needs.
Conclusion: Building a Future-Ready PAM Program
Advancing your PAM maturity is not just about deploying a tool – it’s about developing a long-term strategy that evolves with your organization’s needs. By progressing through the stages of the PAM Maturity Model, you can create a resilient program that effectively protects your critical systems, data, and identities.
However, the journey to full PAM maturity can be complex. As your organization’s security landscape evolves, balancing strategic objectives, automation, and advanced security controls becomes increasingly challenging. That’s where expert guidance is crucial.
At iC Consult, we have successfully delivered over 200 PAM projects, helping organizations of all sizes build tailored, effective PAM programs. No matter where you are on your PAM maturity journey, our experts are ready to support you every step of the way.
Learn more about our PAM services or contact us today to get expert assistance in building a stronger, more secure PAM program for your organization.


