How enterprises can protect their MCP ecosystems with identity-first strategies
Large Language Models (LLMs) and AI agents have fundamentally changed how we interact with information and services online. Organizations across industries are now seeking standardized, scalable ways to expose their products and services to this “new user” — the AI agent.
The Model Context Protocol (MCP), open-sourced by Anthropic in November 2024, is emerging as a promising standard to streamline and scale this type of connectivity. However, taking MCP servers into production introduces significant identity and security challenges.
This blogpost outlines the core security hurdles enterprises face with MCP—and provides actionable identity recommendations to build secure, scalable MCP servers.
MCP 101 – A Quick Overview
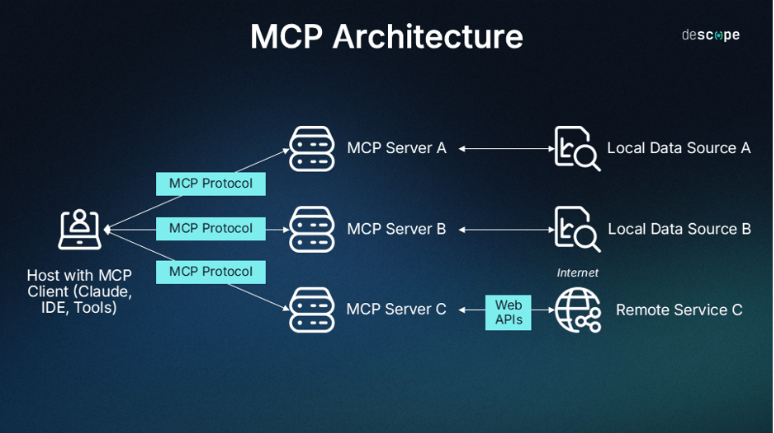
MCP provides a standardized way for LLMs and AI agents to connect with external data sources and tools, akin to a “universal remote” for AI. It:
- Defines a format to describe tools (functions) across any AI system
- Provides a protocol for discovering and executing those tools
- Enables cross-system tool use without custom integration code
Core MCP components:
- MCP client – embedded in AI tools like LLMs and handles connections (e.g., Claude Desktop)
- MCP server – exposes tools and context for discovery and usage (e.g., Stripe MCP server)
- Transport layer – manages communication between clients and servers (via HTTP + SSE or stdin/stdout)
While any organization can build an MCP server, implementing one securely and at scale is a complex task.
Enterprise Challenges in MCP Adoption
Enterprise MCP projects often encounter five key identity-related hurdles:
1. OAuth Compliance
MCP specifies OAuth 2.1 for authorization, requiring robust implementation of PKCE, Dynamic Client Registration (DCR), and other advanced flows—often a heavy lift for enterprise teams.
2. Fine-Grained Permissions
MCP favors scope-based permissions. A CRM MCP server might need separate scopes for “read contacts”, “update deals”, or “export contact lists”—even if they access the same backend API.
3. Token Lifecycle Management
Enterprises must track which users or agents hold which tokens, what scopes those tokens grant, and how tokens are refreshed or revoked.
4. Auth and SSO Integration
MCP servers should be protected via user authentication—ideally with SSO for employees and external partners. However, native SSO support is currently missing from the MCP spec.
5. Lack of Visibility
Enterprises need centralized insight into AI agent activity, including agent registration, verification status, granted scopes, and audit trails—essential for security and compliance.
Best Practices to Secure MCP Servers
To address these challenges, Descope recommends the following identity strategies:
Use External Authorization Servers
MCP servers should act solely as Resource Servers. Delegate OAuth flows to a central identity provider. Point MCP servers to that provider’s metadata for seamless OAuth integration.
Implement Tool-Level Scopes
Rather than tying scopes to APIs, validate access at the function or tool level. Start with minimum viable scopes and expand progressively. Offer users consent screens for transparency.
Harden DCR Workflows
Restrict DCR access to trusted IP ranges or VPNs. Enforce allowlists for redirect URls. Differentiate verification flows for public vs. confidential clients. Use short-lived sessions.
Design for SSO
Even if not natively supported in MCP, enterprises should architect SSO readiness into their environments. Use identity federation for internal and external access.
Establish Agent Visibility
Log and monitor all agent interactions. Maintain detailed records of granted scopes, agent identity status, and access behavior to support audits.
Conclusion
MCP opens powerful new capabilities for enterprise AI integration—but security and identity must be foundational from the start. By implementing OAuth 2.1, permission granularity, and federated access, organizations can fully leverage MCP while staying secure.
Descope’s Agentic Identity Hub and Control Plane offer key components to build this foundation. As part of the broader identity ecosystem, iC Consult supports clients globally in deploying these concepts securely and at scale.
